Bake that Book
Last Summer i gave my old Macbook Pro 15″, Late 2011 with 8GB and 160GB SSD to a friend, since i got a Retina upgrade. I think the old one was still decent, since the SSD gave it that boost to make it usable, even if the laptop was 2 years old at that time. Unluckily the old Macbook Pro didn’t last long, it just died after 3 month. Wouldn’t turn on anymore. As i predicted, after bringing it to the Apple Store, they said the logic board was fried, which always means its totaled. We bought a new Macbook and moved on.
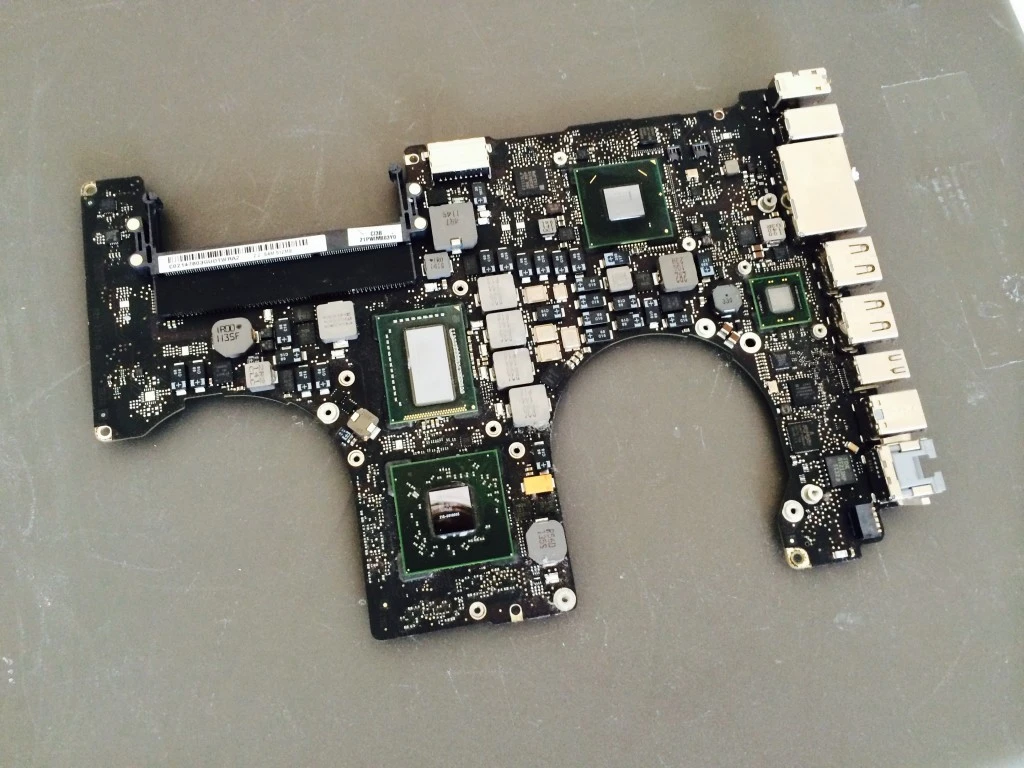
Now i got the broken Macbook back to my place and i thought i would at least sell the display, case and reuse the SSD. But i remembered reading all the Macbook baking blog articles. I already disassembled a few Macbooks down to the logic board and also did some reflow stuff for side projects. Also knowing that a friend of mine has good experience with baking old Nokia phones, i though i give it a try.
- Go to ifixt.com and look up the tutorial to change the logic board
- Disassemble the laptop, collect screws and parts in separate containers
- Be becareful with all the ribbon cable connectors, there are a lot and some are tricky
- Get the logic board out, remove heat pipes, ram and speakers
- Preheat oven to 180c
- I cleaned the board with isopropyl alcohol
- Set board on tin foil legs on a baking tray
- Put in the oven for 7 minutes
- Let it cool fast at a open window
- Clean fans and case from the inside
- Assemble, make sure to get all cables connected
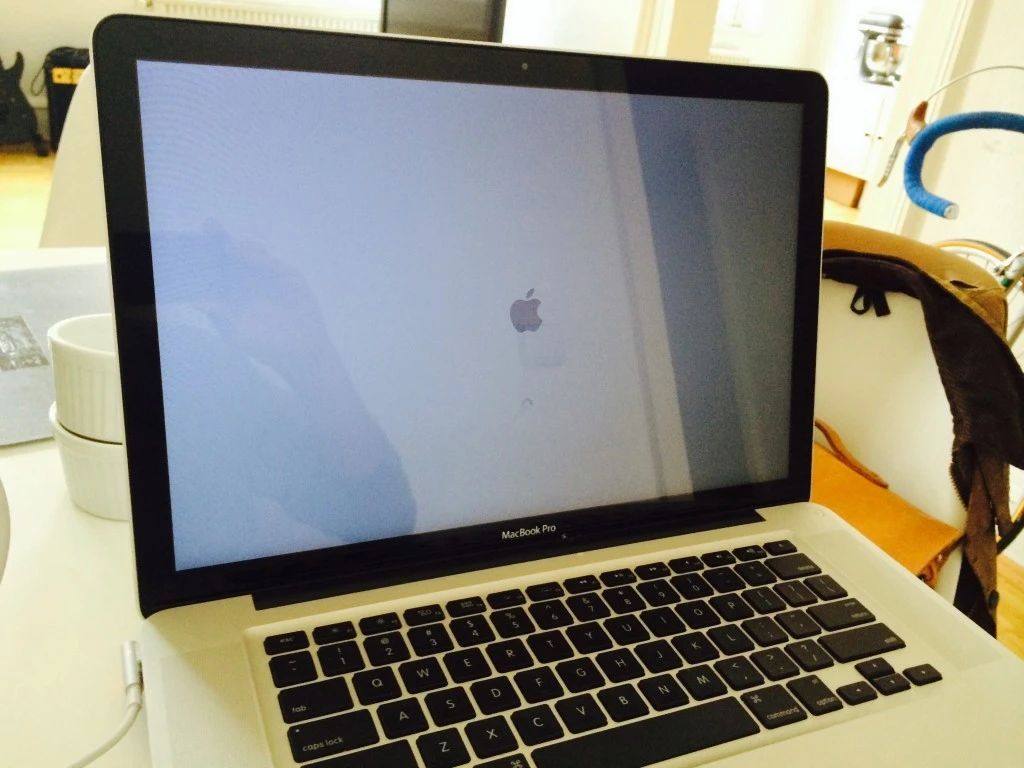
- Boot that Book
I hoped that i had a 50/50 chance that it will work. I was confident, that i don’t mess the laptop during disassemble and assemble phase, i wasn’t sure what the result was after baking. I remembered that the laptop got quite hot while working, so there were some odds that this permanent heat would have altered the setup of the parts of the pcb. And it turned out to be worth the work, the Macbook booted up nicely.